Curated list of awesome kubectl plugins

When you followed my last blog post, you're having kubectl and krew installed by now. These two tools are a requirement for this blog post, so if you don't have them installed yet, please follow the instructions there first.
Basic krew commands
To follow this article you should also be familiar with krew as the plugin manager for kubectl. If you don't know krew yet, check out this blog post.
List of krew plugins
RBAC-related plugins
krew install access-matrix |
rakkess |
|
krew install rbac-lookup |
kubectl rbac-lookup |
|
krew install rbac-view |
kubectl rbac-view |
|
krew install rolesum |
kubectl rolesum |
|
krew install who-can |
kubectl who-can |
|
krew install whoami |
kubectl-whoami |
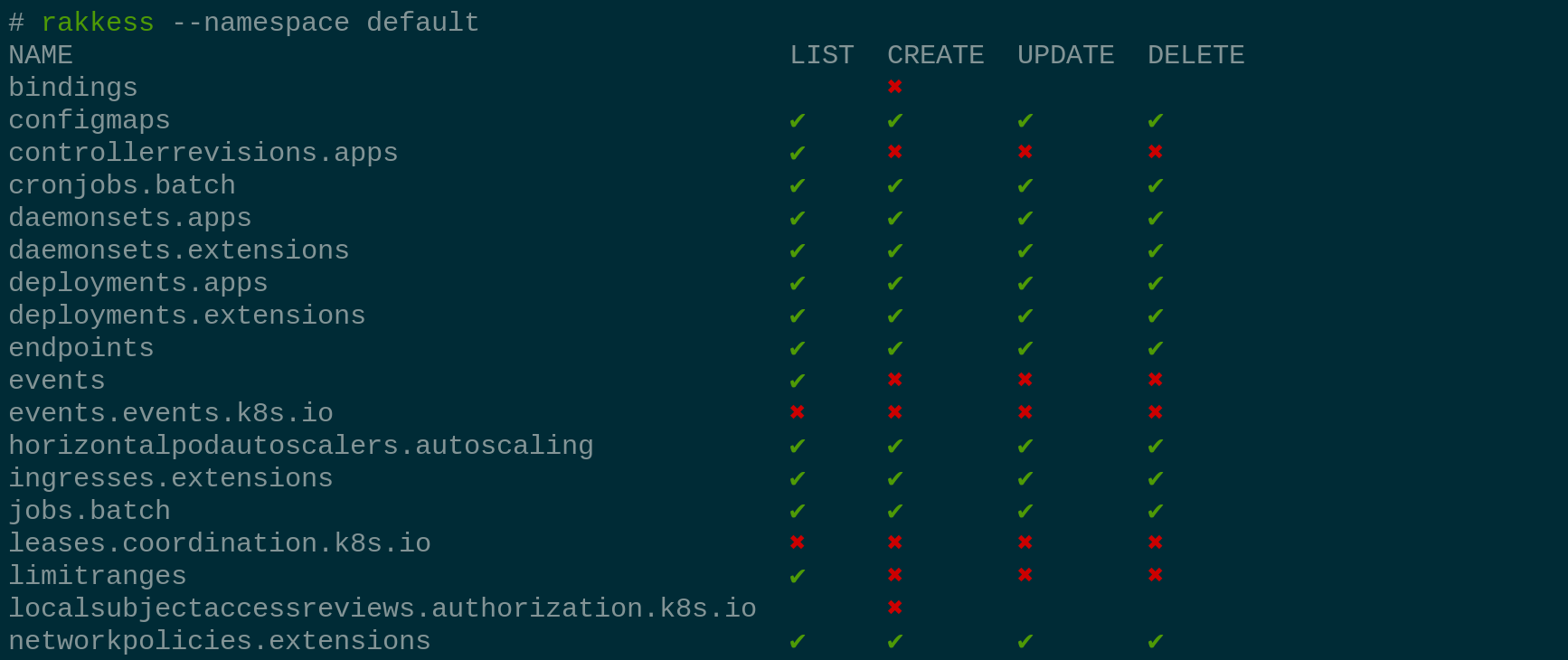
access-matrix
krew install access-matrixWhen you are working on a Kubernetes cluster, you may not know which access rights you have. With rakkess you get a complete overview of your access rights at cluster scope. With additional flags this can be narrowed done by namespace (--namespace) or performed action (--verbs). Additionally the overview can be generated for other entities like users (--as) or service accounts (--sa). Another nice feature is the possibility to generate a matrix of all service accounts, groups and users with their access rights to specfic resources: rakkess resource configmaps.
rbac-lookup
krew install rbac-lookupIf you are more interested in roles and their bindings to subjects, you should take a look at rbac-lookup from Fairwinds. A complete list of all bindings can be generated by using kubectl rbac-lookup. This can be narrowed down by the --kind flag to list only bindings to a subject of the type user, group or serviceaccount. You can also append a string to the command to perform a grep-like search on the subject name.
kubectl rbac-lookup kube-proxy
SUBJECT SCOPE ROLE
kube-system:kube-proxy cluster-wide ClusterRole/system:node-proxier
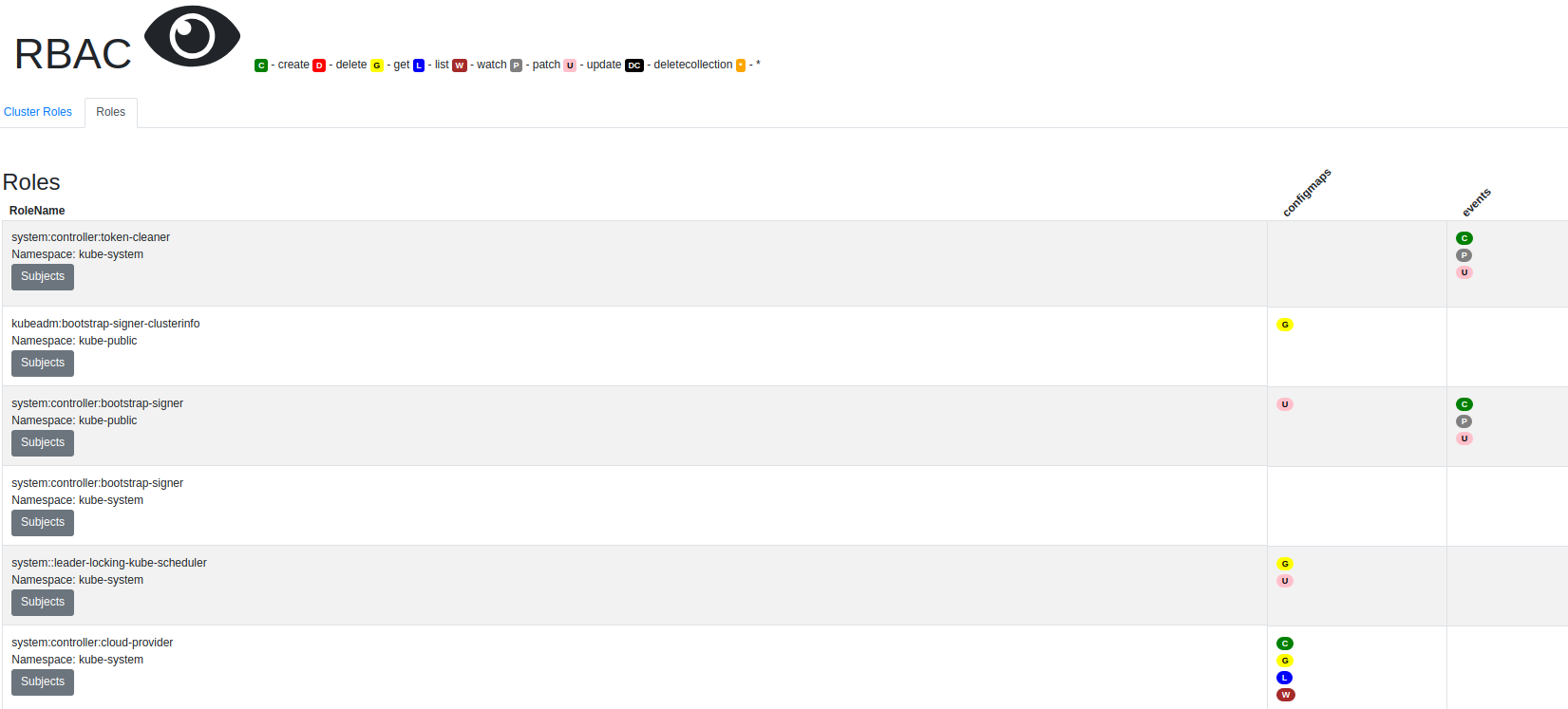
system:kube-proxy cluster-wide ClusterRole/system:node-proxierrbac-view
krew install rbac-viewRbac-view is the most convenient way to visualize all Roles and ClusterRoles defined a Kubernetes cluster. By typing kubectl rbac-view a web application is started, that can be used through your browser. It lists all Roles and ClusterRoles with their allowed actions on the different resource types defined inside the cluster. The result list can be filtered by the name of the (Cluster)Role and the name of the resource.
rolesum
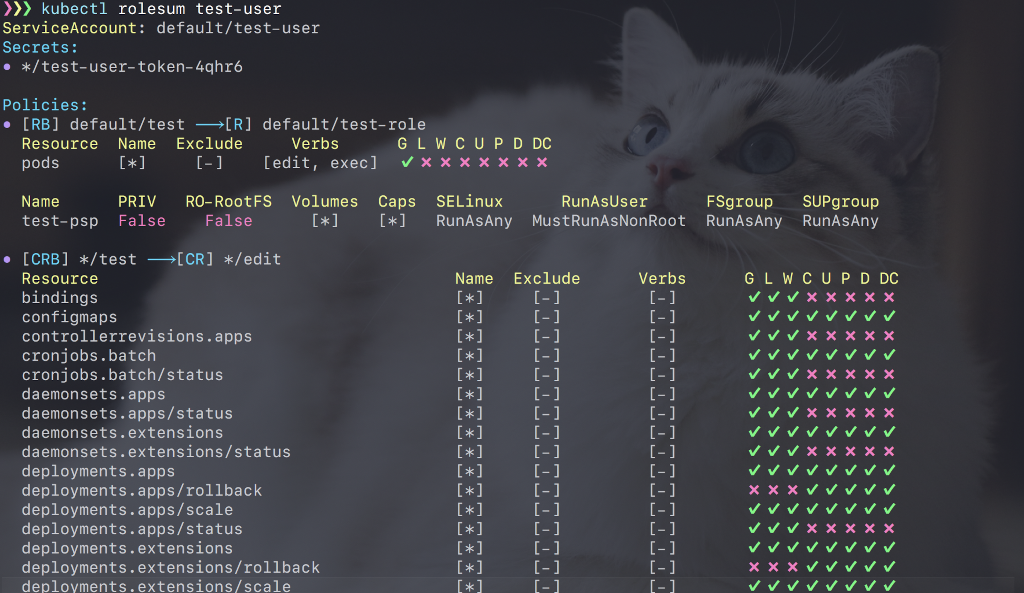
krew install rolesumBy default kubectl rolesum ${SUBJECT} shows you the assinged Secrets, PodSecurityPolicies and (Cluster)RoleBindings with the corresponding Permissions of the ServiceAccount ${SUBJECT} of the current namespace. You can set the desired Namespace with the -n flag and set the kind of the subject with the -k flag.
who-can
krew install who-canIf you want to know which subject (User, Group or ServiceAccount) is able to perform a specific action (e.g. read the content of secrets), then kubectl who-can ${VERB} ${RESOURCE} -n ${NAMESPACE} is the perfect solution for you.
kubectl who-can get secret -n default
ROLEBINDING NAMESPACE SUBJECT TYPE SA-NAMESPACE
portainer-rb-7f7d709e-b561-4abc-88f5-d87a3171ddca-default default portainer-sa-user-7f7d709e-b561-4abc-88f5-d87a3171ddca-2 ServiceAccount portainer
CLUSTERROLEBINDING SUBJECT TYPE SA-NAMESPACE
argo-rollouts argo-rollouts ServiceAccount argo
argocd-application-controller argocd-application-controller ServiceAccount argocdwhoami
krew install whoamiWorks the same way whoami does on any Linux distributions and displays you the username of the subject you are currently authenticated as.
kubectl whoami
kubernetes-adminSecurity-related
| Plugin name | Install command | Usage command |
|---|---|---|
| advise-policy | krew install advise-policy |
kubectl advise-policy |
| advise-psp | krew install advise-psp |
kubectl advise-psp |
| apparmor-manager | krew install apparmor-manager |
kubectl apparmor-manager |
| kubesec-scan | krew install kubesec-scan |
kubectl kubesec-scan |
| popeye | krew install popeye |
kubectl popeye |
| psp-util | krew install psp-util |
kubectl psp-util |
| score | krew install score |
kubectl score |
| starboard | krew install starboard |
kubectl starboard |
advise-psp
krew install advise-pspapparmor-manager
krew install apparmor-managerkubesec-scan
krew install kubesec-scanpopeye
krew install popeyepsp-util
krew install psp-utilscore
krew install scorestarboard
krew install starboardIngress-related
krew install cert-manager |
kubectl cert-manager |
cert-manager
krew install cert-managerWith this cli tool you are able to manage and configure cert-manager resources. You can approve, create or deny CertificateRequests. Very handy is the inspection of already generated Certificates that are stored inside of TLS-secrets using kubectl cert-manager inspect secret ${TLS_SECRET_NAME}. Additional informations about a certificate can be display with kubectl cert-manager status certificate ${CERTIFICATE_NAME}.
Network-related
krew install np-viewer |
kubectl np-viewer |
|
krew install sniff |
kubectl sniff |
np-viewer
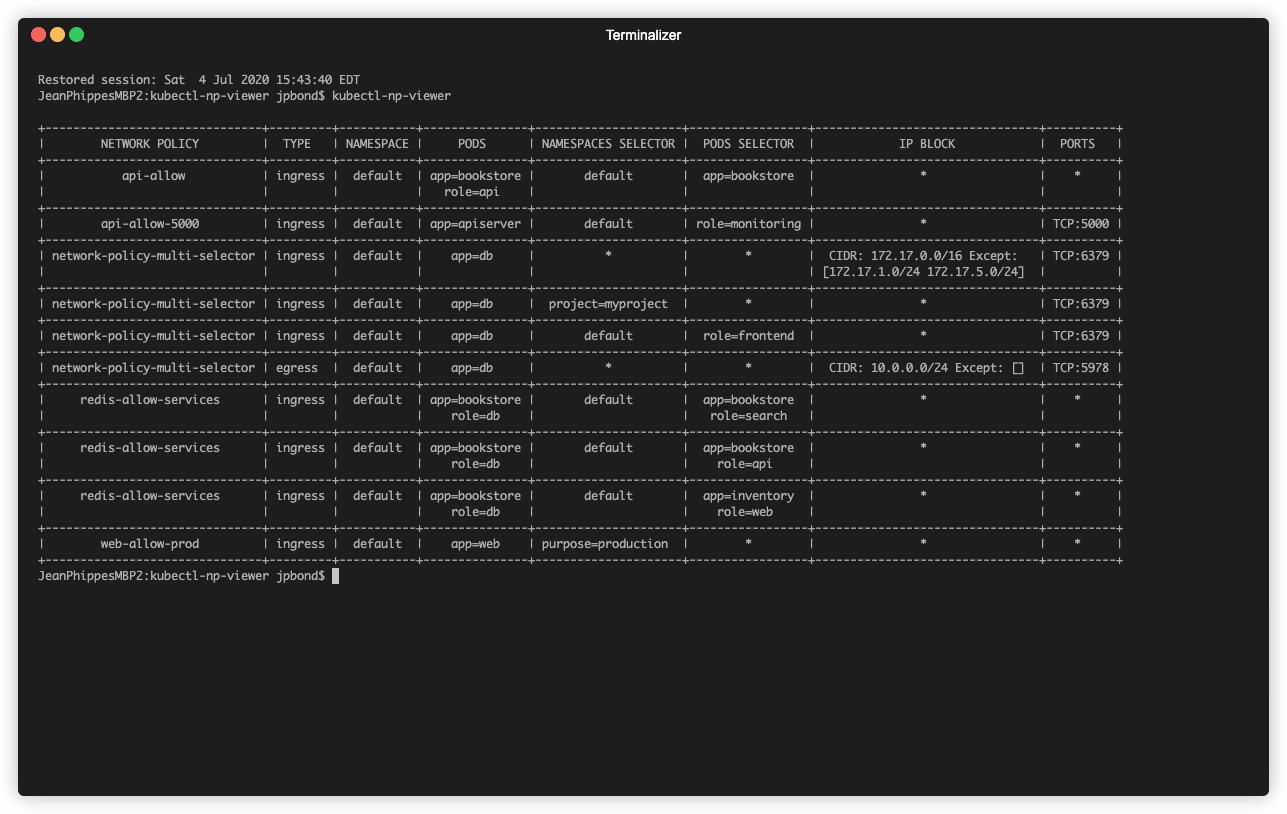
krew install np-viewerNetwork Policies are a great way to build a firewall-like protection layer for your Kubernetes cluster on layer 3 and 4. When the number of policies rises it is quite hard to debug network-related problems in your Cluster. kubectl np-viewer gives you a nice overview off all defined Policies showing you all the informations you need to understand the allowed network traffic. The list can be limited to a specific type (-ifor Ingress; -e for Egress), a namespace (-n for single, -A for all) or a Pod (-p).
sniff
krew install sniffWorking in a distributed environment like Kubernetes clusters usually are makes it sometimes extremly hard to analyse the network traffic of a specific microservice and its dependencies. With sniff you are able to utilize tcpdump and wireshark to capture the network traffic of any pod. Check out a demo here.
Debugging-related
| Plugin name | Install command | Usage command |
|---|---|---|
| flame | krew install flame |
kubectl flame |
| status | krew install status |
kubectl status |
| stern | krew install stern |
kubectl stern |
| tail | krew install tail |
kubectl tail |
| trace | krew install trace |
kubectl trace |
flame
krew install advise-pspstatus
krew install statusstern
krew install sterntail
krew install tailtrace
krew install traceHelper
| Plugin name | Install command | Usage command |
|---|---|---|
| ctx | krew install ctx |
kubectx and kubens |
| get-all | krew install get-all |
kubectl get-all |
| topology | krew install topology |
kubectl topology |
| tree | krew install tree |
kubectl tree |
ctx
krew install ctxWhen working with multiple clusters and/or namespaces it becomes a tedious task to switch between clusters and/or namespaces. But ctx can help with this problem. It provides two commands kubectx and kubens to easily switch namespace and/or context.
get-all
krew install get-allKubernetes offers a command kubectl get all, which gives you a good overview of deployed Kubernetes objects. But it doesn't include all objects as the name might suggest and is limited to the workload-part showing DaemonSets, Deployments, Pods, Replicasets, Services and StatefulSets only. If you need a overview of really all resources inside your cluster or a single namespace (--namespace) get-all comes to the rescue. If you need to exclude some resources you can use the --exclude flag. Additionally you can limit the output to resources of the cluster or namespace scope using the --only-scope flag.
kubectl get-all --only-scope=namespace -n default
NAME NAMESPACE AGE
configmap/kube-root-ca.crt default 231d
endpoints/kubernetes default 231d
secret/default-token-bj2g6 default 231d
serviceaccount/default default 231d
service/kubernetes default 231dtopology
krew install topologyProduction-ready clusters are often build across multiple regions and availability zones. You can get insights into the distributions of nodes and pods using kubectl topology node respectively kubectl topology pod. Of course the list can be limited to a single namespace (-n).
kubectl topology pod -n ingress-nginx
NAMESPACE NAME NODE REGION ZONE
ingress-nginx cert-manager-55db7cf6cd-d2d5j k8s6p eu-central-3 eu-central-3a
ingress-nginx cert-manager-cainjector-6bc9d758b-88gtr k8s4p eu-central-1 eu-central-1b
ingress-nginx cert-manager-webhook-9865f6cd7-p2djk k8s4p eu-central-1 eu-central-1b
ingress-nginx ingress-nginx-controller-756f546d89-pxvqh k8s5p eu-central-2 eu-central-2ctree
krew install treeIf you are interested in the parent-child relationships between resources kubectl tree ${KIND} ${NAME} is there to help.
kubectl tree deployments ingress-nginx-controller -n ingress-nginx
NAMESPACE NAME READY REASON AGE
ingress-nginx Deployment/ingress-nginx-controller - 68d
ingress-nginx └─ReplicaSet/ingress-nginx-controller-756f546d89 - 68d
ingress-nginx └─Pod/ingress-nginx-controller-756f546d89-pxvqh True 2d2h
ingress-nginx └─CiliumEndpoint/ingress-nginx-controller-756f546d89-pxvqh - 2d2hMaintenance-related
| Plugin name | Install command | Usage command |
|---|---|---|
| cost | krew install cost |
kubectl cost |
| deprecations | krew install deprecations |
kubectl kubepug |
| df-pv | krew install df-pv |
kubectl df-pv |
| images | krew install images |
kubectl images |
| ktop | krew install ktop |
kubectl ktop |
| node-restart | krew install node-restart |
kubectl node-restart |
| outdated | krew install outdated |
kubectl outdated |
| prune-unused | krew install prune-unused |
kubectl prune-unused |
| resource-capacity | krew install resource-capacity |
kubectl resource-capacity |
| sick-pods | krew install sick-pods |
kubectl sick-pods |
| unused-volumes | krew install unused-volumes |
kubectl unused-volumes |
| view-allocations | krew install view-allocations |
kubectl view-allocations |
| view-utilization | krew install view-utilization |
kubectl view-utilization |
| vpa-recommendation | krew install vpa-recommendation |
kubectl vpa-recommendation |
cost
krew install costBuild on top of kubecost this plugin tells you how much money you've spend on your Kubernetes workloads. These cost informations can be aggregated by namespace, deployment, controller, label, pod and node. The costs can be viewed historical but also be calculated for a time window in the future.
kubectl cost node --historical --window 7d --show-cpu --show-memory
+-------------+---------------------------------------------+---------------+--------------+---------------+
| CLUSTER | NAME | CPU COST | RAM COST | TOTAL COST |
+-------------+---------------------------------------------+---------------+--------------+---------------+
| cluster-one | gke-test-cluster-default-pool-d6266c7c-dqms | 4.128570 | 2.128920 | 6.257491 |
| | gke-test-cluster-pool-1-9bb98ef8-3w6g | 4.128570 | 2.128920 | 6.257491 |
| | gke-test-cluster-pool-1-9bb98ef8-cf3j | 4.128570 | 2.128924 | 6.257495 |
| | gke-test-cluster-pool-1-9bb98ef8-kdsf | 4.128570 | 2.128924 | 6.257495 |
+-------------+---------------------------------------------+---------------+--------------+---------------+
| SUMMED | | USD 16.514280 | USD 8.515688 | USD 25.029972 |
+-------------+---------------------------------------------+---------------+--------------+---------------+deprecations
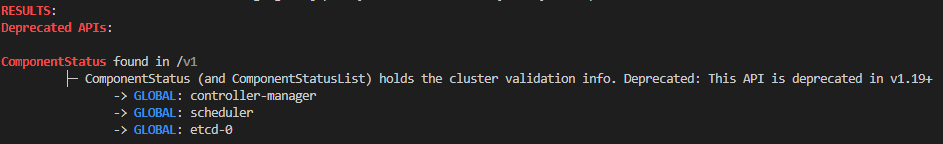
krew install deprecationsKubernetes is incredible fast-paced in evolving and therefore deprecates APIs quite often. To check if you are using deprecated objects inside your cluster just run kubectl deprecations. This tool can also be integrated into your CI/CD-pipelines to identify the usage of old APIs inside your HELM charts e.g.
df-pv
krew install df-pvManaging and providing storage is a complicated admin task in Kubernetes. With df-pv you can check existing PersistentVolumes and their size, already used and still available space and many more.
PV NAME PVC NAME NAMESPACE NODE NAME POD NAME VOLUME MOUNT NAME SIZE USED AVAILABLE %USED IUSED IFREE %IUSED
pvc-31ee2c56-e4ac-422e-836f-5fb4ed9628c2 grafana monitoring node02 grafana-54f578f88c-bjd26 storage 9Gi 507Mi 9Gi 5.08 205 655155 0.03images
krew install imagesThe number of used images inside a Kubernetes cluster quickly reaches 100 and more. To get an overview of all available images and their respective version you can use kubectl images. Can be limited to a single namespace (-n) or all namespaces (-A). You can even change the output-format from table to json using -o and the displayed colums (-c).
kubectl images -n ingress-nginx -c 0,1,2,3
[Summary]: 1 namespaces, 4 pods, 4 containers and 4 different images
+---------------+-------------------------------------------+---------------+--------------------------------------------------------------------------------------------------------------------+
| Namespace | PodName | ContainerName | ContainerImage |
+---------------+-------------------------------------------+---------------+--------------------------------------------------------------------------------------------------------------------+
| ingress-nginx | cert-manager-55db7cf6cd-d2d5j | cert-manager | quay.io/jetstack/cert-manager-controller:v1.8.0 |
+ +-------------------------------------------+ +--------------------------------------------------------------------------------------------------------------------+
| | cert-manager-cainjector-6bc9d758b-88gtr | | quay.io/jetstack/cert-manager-cainjector:v1.8.0 |
+ +-------------------------------------------+ +--------------------------------------------------------------------------------------------------------------------+
| | cert-manager-webhook-9865f6cd7-p2djk | | quay.io/jetstack/cert-manager-webhook:v1.8.0 |
+ +-------------------------------------------+---------------+--------------------------------------------------------------------------------------------------------------------+
| | ingress-nginx-controller-756f546d89-pxvqh | controller | k8s.gcr.io/ingress-nginx/controller:v1.1.3@sha256:31f47c1e202b39fadecf822a9b76370bd4baed199a005b3e7d4d1455f4fd3fe2 |
+---------------+-------------------------------------------+---------------+--------------------------------------------------------------------------------------------------------------------+ktop
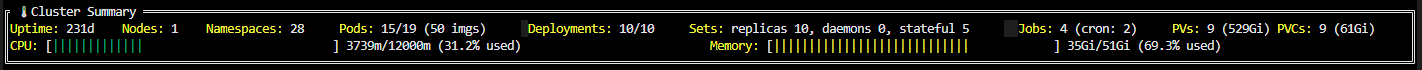
krew install ktopktop works just like it's "big brother" top you may know already from the Linux world. It displays usefule metrics about nodes, pods and other workloads running in your Kubernetes cluster. Metrics can be displayed cluster-wide or namespace-scoped (--namespace). Besides these metrics for nodes and workloads it also presents a cluster summary.
node-restart
krew install node-restartWith this plugin you are able to restart your Kubernetes cluster in a graceful way as it performs a rolling restart of all or a subset of nodes. The subset can be defined by using the label selector. Additionally you can set a delay between the restarts to give the nodes some to time to come fully back.
kubectl node-restart --selector node-role.kubernetes.io/master --sleep 120outdated
krew install outdatedOutdated is a very simple but handy plugin that searches all namespaces you have at least read access to for out-of-date images running in your Kubernetes cluster.

prune-unused
krew install prune-unusedresource-capacity
krew install resource-capacitysick-pods
krew install sick-podsunused-volumes
krew install unused-volumesview-allocations
krew install view-allocationsview-utilization
krew install view-utilizationvpa-recommendation
krew install vpa-recommendation